Mail Threat Defense S400
Secure Email Against Targeted Phishing Attacks
Defeats Targeted Attacks
- Ability to identify attacks in embedded file attachments and URL links
- Delivers screened and sanitized email messages to end users
Eliminates Known Attacks
- Uses sophisticated techniques to quickly identify both known bad and good files and URLs
- Leverages the Global Intelligence Network to stay up-to-date on the latest threats
Uncovers New Attacks
- Uses precise detonation chambers to uncover new, zero-day attacks. Understands the risk level of new attacks with targeted malicious risk scoring
Provides Configurable Security Policies
- Supports the unique security enforcement need of the organization
- Balances message delivery speed, user autonomy desires and business needs
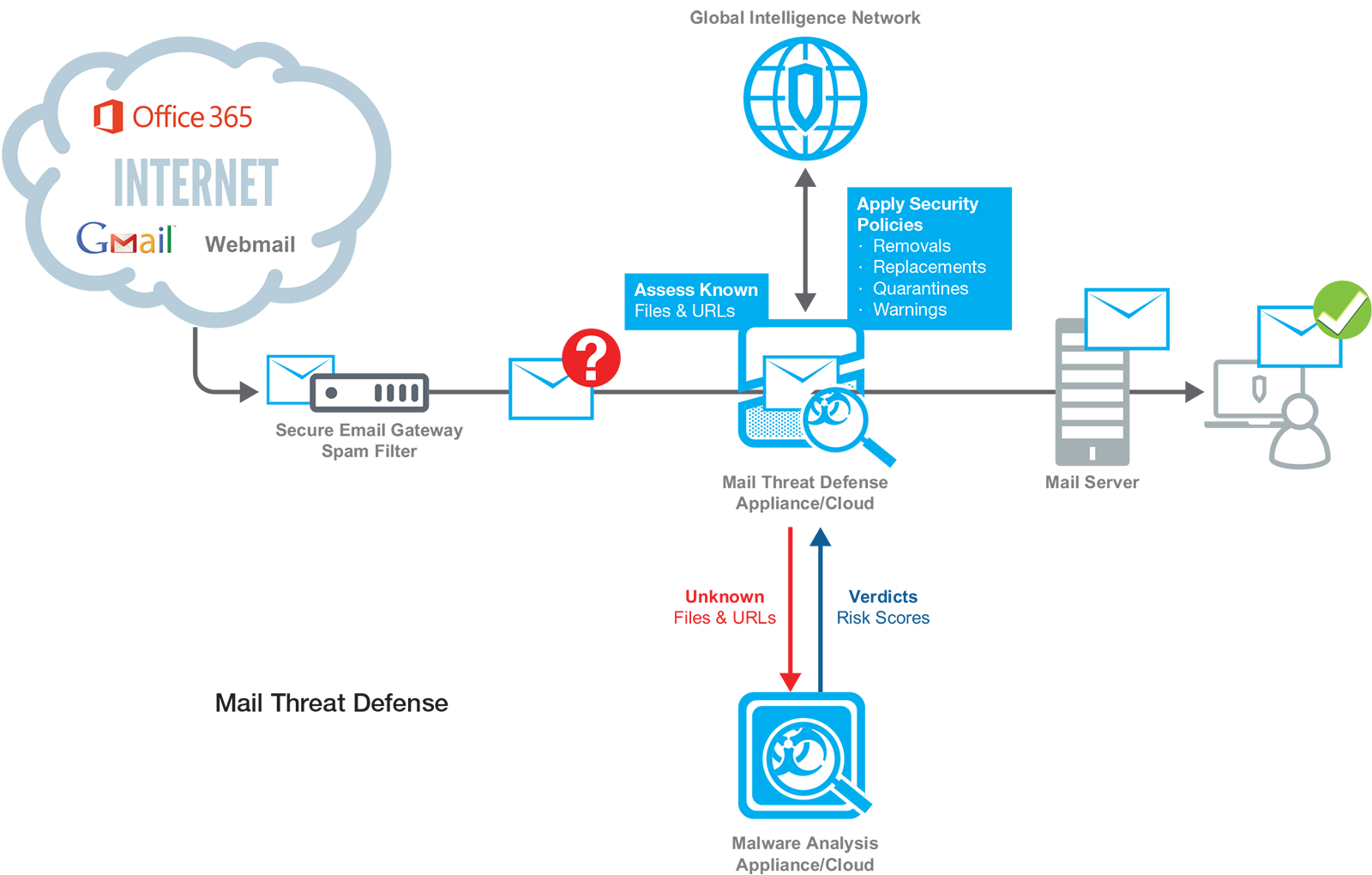
Email is one of the most common attack vectors used by hackers to get into your corporate network. Attackers will send targeted communications “phishing” for information they can use to perpetrate other attacks and establish a foothold in your organization they can use to spread. They may try to trick your users into providing sensitive data – such as usernames and passwords, financial records, etc. – or get them to click on a link or open a file that contains malicious code that automatically infects the endpoint. To protect against these types of attacks, you need a solution that is capable of identifying and preventing the varied phishing methods attackers deploy – you need Blue Coat Mail Threat Defense.
Blue Coat Mail Threat Defense protects against email-borne malware in links and attachments that are activated by unsuspecting end users. The solution can identify and extract malicious content from an email before it is delivered to the user to neutralize the attack. As a result, you can effectively enforce corporate security policies and keep your resources safe, without impacting the user’s experience.
Blue Coat Defeats Targeted Attacks
Mail Threat Defense inspects and analyzes all email messages for malicious content before they arrive in the targeted user’s in-box. If there is malware contained within embedded URL links or file attachments, Mail Threat Defense will identify it and actively block, alter, or quarantine the message, based on the severity of the threat and your corporate security policy. The solution has no impact on the user experience, beyond ensuring they only receive sanitized, safe messages in their inbox.
Eliminates Known Attacks
Mail Threat Defense scans embedded file attachments and URL links to identify known malware and takes action based on your corporate security policy. The solution also identifies files and URLs that are known to be good and sends those safe messages on to the user. Mail Threat Defense applies a variety of sophisticated techniques to quickly identify both known bad and good files and URLs, including:
- URL Filtering
- File Hash Reputation
- Anti-Virus Detection
- Static Code Analysis
The solution leverages the Blue Coat Global Intelligence Network, which collects and analyzes over a billion previously uncategorized new web requests a day from our 15,000 enterprise customers and their millions of users accessing the Internet daily.
Uncovers New Attacks
Mail Threat Defense can identify never-beforeseen, unique and zero-day malware. It extracts any unknown files and URLs it detects and sends them to Blue Coat Malware Analysis for identification and risk scoring. Malware Analysis is an advanced, multi-stage sandbox that uses precisely tailored, gold-image detonation chambers to perform recursive analysis on any primary files or URLs, plus any subsequent “dropped” files and callback URLs. It uses:
- Static Code Analysis
- Dynamic/Behavioral Analysis
- Reputational Analysis
- YARA Rules Analysis
The solution will then provide a targeted risk score for the malware it has discovered, so you can effectively address and mitigate the risk posed by this previously unknown threat.
Provides Configurable Security Policies
The security policies of Mail Threat Defense enable you to balance message delivery speed, user autonomy desires and business security needs. Based on the verdicts and malicious risk scores determined by the solution, you can enact policies that block, alter, quarantine or detect / alert on the malware. As a result, you can:
- Remove malicious attachments
- Remove / Replace malicious links
- Add malicious content warnings
- Quarantine malicious messages
Deployment Modes
The solution can be deployed inline, as a cloud-based service or an on-premises appliance. It is typically positioned behind the firewall, after the SPAM filter, to ensure it can inspect all mail before it is delivered to the user. Note, the solution can also be deployed passively, alerting you as soon as email malware is detected. It seamlessly integrates with any other email security solutions you have to preserve and enhance the value of your investments.