CounterBreach
Imperva CounterBreach protects enterprise data stored in enterprise databases, file shares and cloud applications from the theft and loss caused by compromised, careless or malicious users. By dynamically learning users’ normal data access patterns and then identifying inappropriate or abusive access activity, CounterBreach proactively alerts IT teams to dangerous behavior.
Protect Your Data from Insider Threats
The greatest threat to enterprise security is the people already on the payroll. To do their jobs, employees, contractors, consultants and vendors must have legitimate access to sensitive and valuable data stored in enterprise databases, file shares and SaaS applications. However, when insiders abuse this access, or when insiders are exploited by outside attackers, enterprise data is exposed. Detection and containment of insider threats requires an expert understanding of both users and how they use enterprise data.
Imperva CounterBreach
Imperva CounterBreach protects enterprise data stored in enterprise databases, file shares and SaaS applications from the theft and loss caused by compromised, careless or malicious users. By dynamically learning users’ normal data access patterns and then identifying inappropriate or abusive access activity, CounterBreach proactively alerts IT teams to dangerous behavior. CounterBreach also uses deception technology to deterministically identify end-point devices that have been compromised by external attackers, adding additional context to user data access learning.
Detect Dangerous User Data Access
CounterBreach detects potential breaches by pinpointing risky data access events and the user associated with the risky access event.
CounterBreach Behavior Analytics
CounterBreach Behavior Analytics uses machine learning and peer group analytics to automatically uncover anomalous data access events. This establishes a full contextual baseline of typical user access to database tables, files stored in file shares and objects stored in cloud apps, and then detects and prioritizes anomalous activity. Combining an expert understanding of users and how they access data equips enterprises with the context and accuracy required to detect data breach incidents. With CounterBreach, security teams can quickly discern between malicious and normal activity so they can immediately identify and act upon risky behavior.
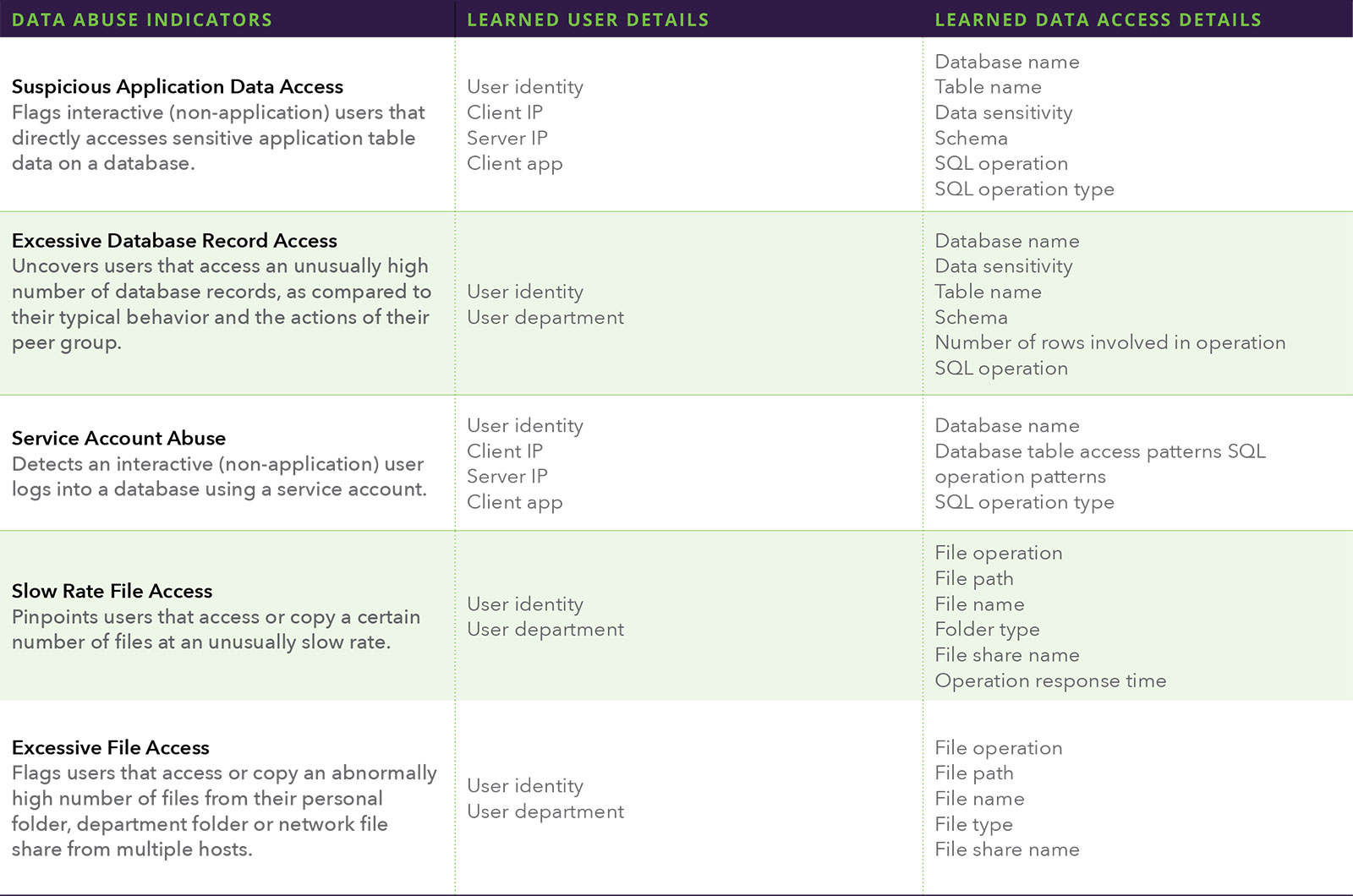
Accurately identifying potential data breaches requires deep contextual understanding of not just user activity, but the data users access and how they access it. Without visibility into the data itself, and an understanding of the indicators of data abuse, one half of the equation is missing. The table below shows examples of common data abuse indicators, and the user and data details needed to do identify them.
CounterBreach Deception Tokens
CounterBreach Deception Tokens detect endpoints compromised by cybercriminals. Once an endpoint is compromised, the threat moves directly from the outside to the inside of the organization. This deterministic identification of compromised endpoints adds additional context to CounterBreach Behavior Analytics.
This patented deception technology lures attackers at the earliest stage of an attack with fictitious information tokens that bad actors probe for upon gaining access to the internal network. Deception tokens include fictitious database credentials, shortcuts to seemingly enticing files and web browser cookies. Deception tokens – which are entirely passive -- are planted on user workstations and appear authentic to the organization and to hackers. Once an attacker attempts to use a Deception Tokens to access data repositories, CounterBreach flags the incident in real-time. The tokens are deterministic in nature, so security teams can ensure that the alerts generated are highly accurate and indicate deliberate intention to access and steal enterprise data.
CounterBreach Key Capabilities
Detect Critical Data Misuse
Incidents detected by Behavior Analytics and Deceptions Tokens are populated into an easy-to-navigate dashboard. CounterBreach spotlights the riskiest users, client hosts and servers so that IT staff can prioritize the most serious data access incidents. Security analysts can also drill down into a view of all open incidents and investigate all the details pertaining to an event.
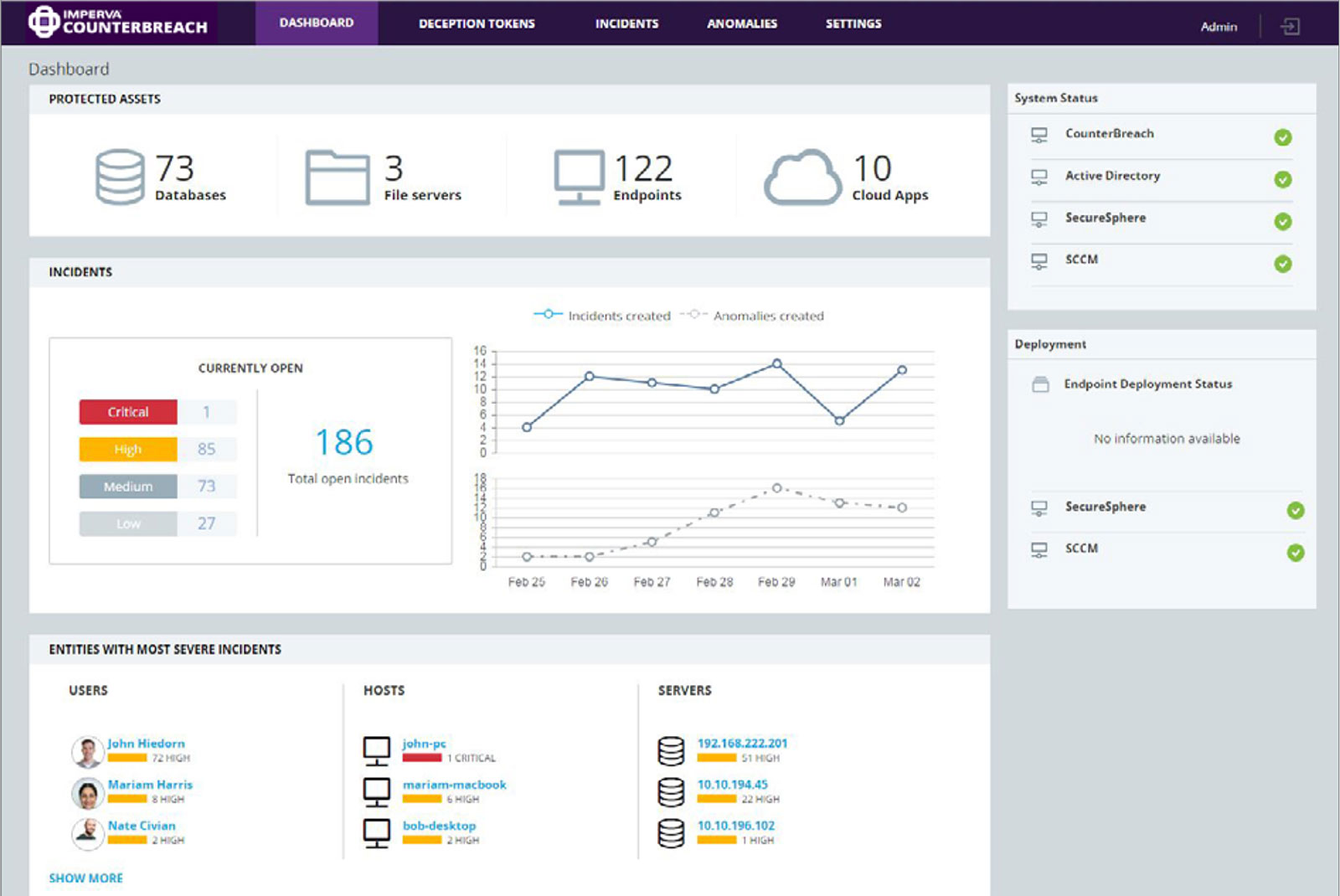
The CounterBreach dashboard aggregates threat indicators across all enterprise data.
Accelerate Incident Response Time
Security teams can efficiently investigate the most risky data access events by filtering open incidents by severity as well as by a specific user, server or client host. Users can then drill deeper into a specific incident to review a detailed description of the event and view granular information about the use and the data that was accessed. From here, SOC staff can close the incident or whitelist behavior that is authorized or unable to be remediated right away.
Simplify Investigations
Security teams can analyze the data access behavior of particular users with the user dashboard. With a consolidated view into database, file and cloud app activity, security analysts have a full picture of the user’s data access across the organization. Security teams can investigate incidents and anomalies specific to the individual, and then drill down to the behavior profile to the view baseline of typical user activity and compare a given user with that user’s peer group.
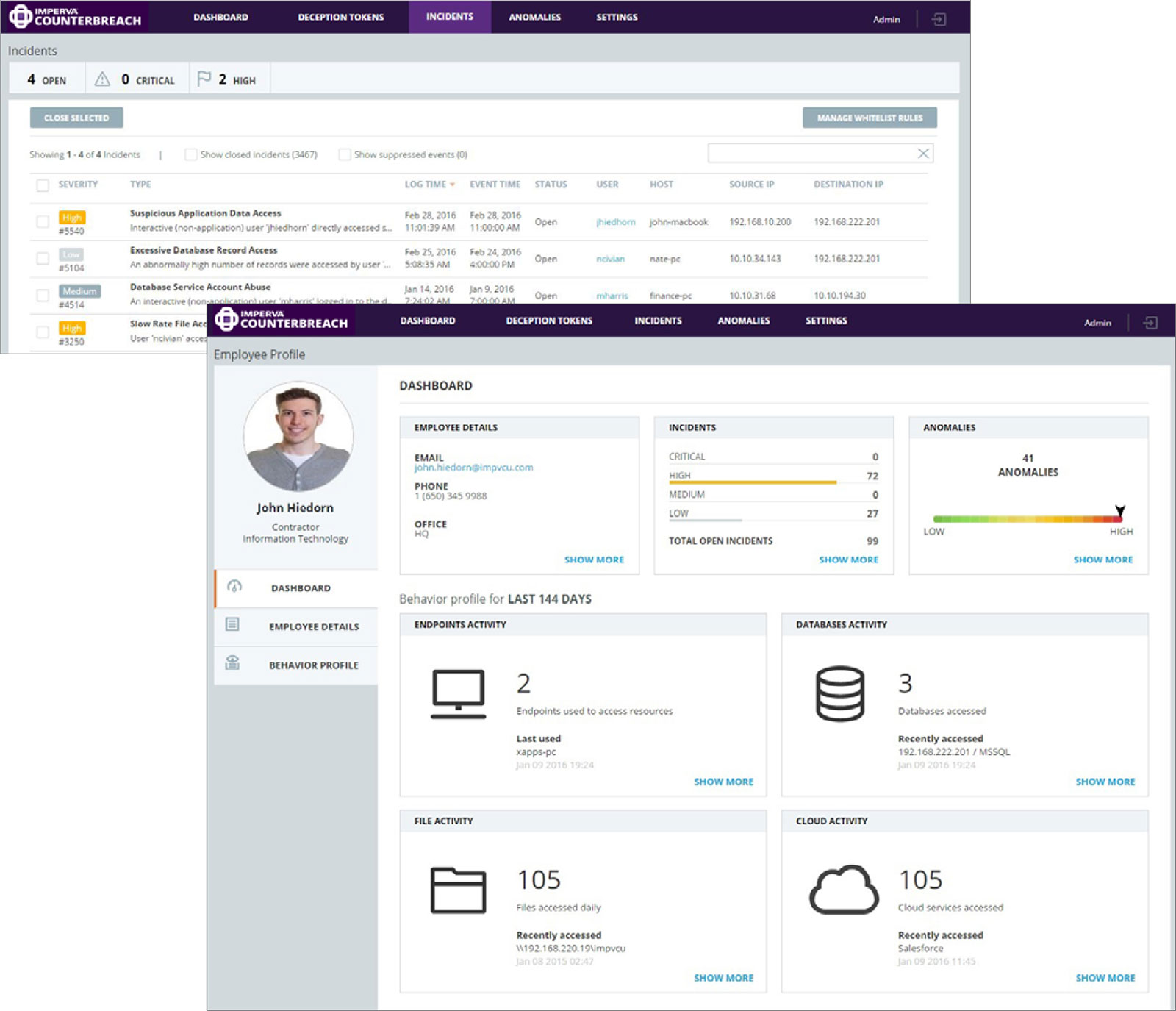
The CounterBreach incident screen shows critical data access anomalies prioritized from critical to low severity.
The CounterBreach user screen provides an at-a-glance look at individual access to enterprise data and highlights risky user behavior
Prevent Data Breaches with Imperva
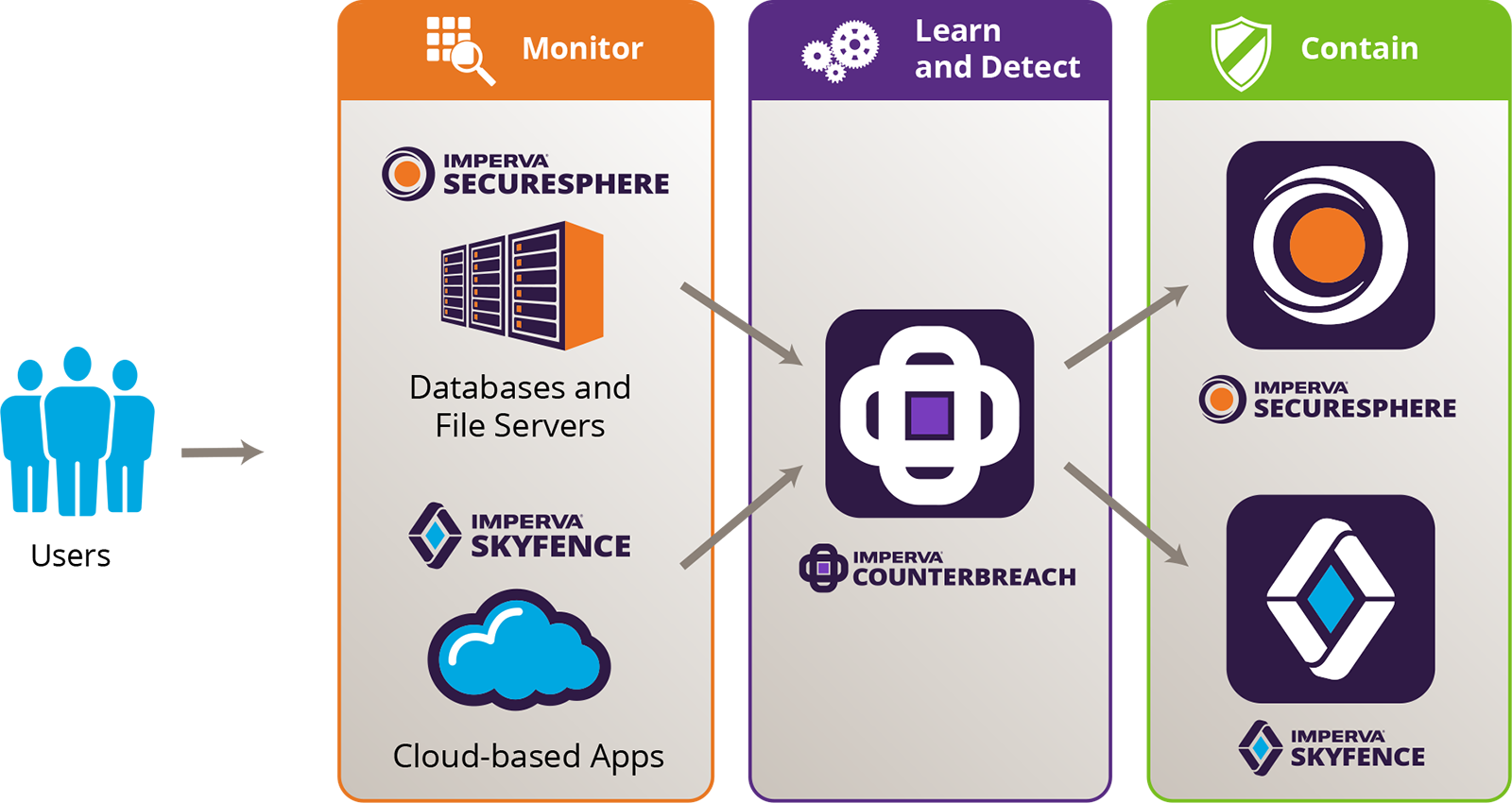
To detect and contain data breaches, organizations need to have visibility into who is accessing enterprise data, understand if that access is legitimate and respond immediately if it’s not. CounterBreach integrates with Imperva SecureSphere and Imperva Skyfence solutions to pinpoint critical anomalies that indicate misuse of enterprise data stored in databases, file servers and cloud apps.
Monitor
Imperva data protection solutions directly monitor all user access to data repositories on-premise or in the cloud. SecureSphere provides visibility into which users access database and file servers, giving IT organizations insight into the ‘who,’ ‘what’ and ‘when’ of access to sensitive information. Skyfence continuously monitors user uploads, downloads and sharing of sensitive data within cloud-based apps such as Office 365, Salesforce and Box.
Learn and Detect
CounterBreach combines Imperva expertise in monitoring and protecting data with advanced machine learning to uncover dangerous user data access activity. Based on granular inputs from SecureSphere and Skyfence, CounterBreach develops a behavioral baseline of typical user data access and then detects critical deviations from the norm. CounterBreach proactively flags these dangerous actions for immediate investigation.
Contain
With the CounterBreach solution, security teams can contain potential data leaks before they become major events. Once dangerous anomalies are detected, enterprises can quickly quarantine risky users in order to proactively prevent or contain data breaches.
System Requirements
CounterBreach Prerequisites
CounterBreach requires one of the following Imperva products performing monitoring and containment functions: SecureSphere Database Activity Monitor, Database Firewall, File Activity Monitor and File Firewall. Additionally, Imperva Skyfence can be integrated with any CounterBreach deployment.
CounterBreach Virtual Appliances
CounterBreach is deployed as virtual appliances that are simple to deploy and do not interfere with existing SecureSphere or Skyfence implementations. The minimum requirements per physical host and for each guest virtual appliance are shown below.
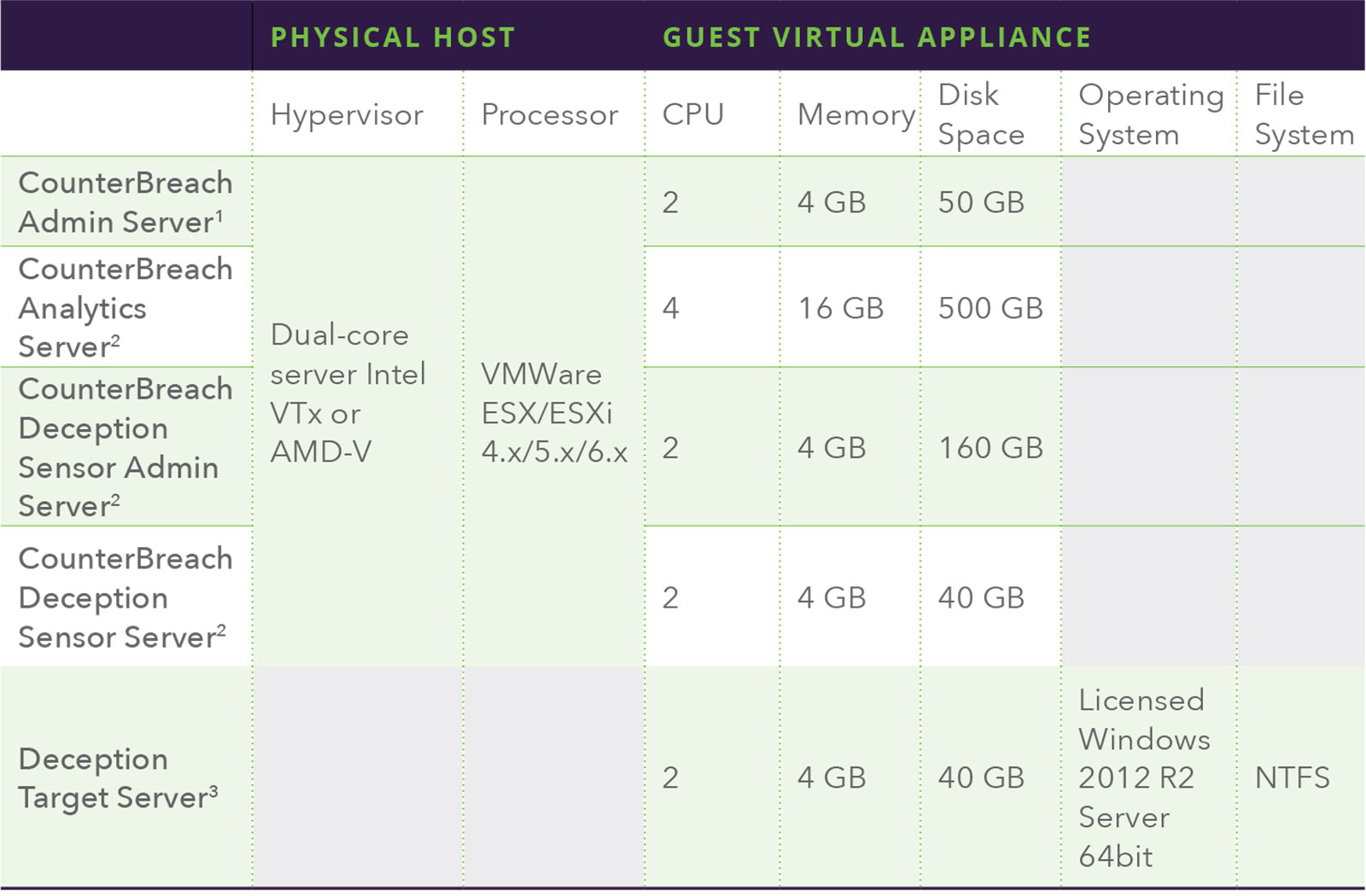
1 The Admin Server is required for Behavior Analytics and Deception Tokens. Imperva will deliver software on pre-configured virtual appliances with the specifications shown above.
2 Imperva will deliver software on pre-configured virtual appliances with the specifications shown above.
3 Imperva will deliver Deception Target software to customers via an installer. A virtual machine with the specifications show above must be provided by the customer.
Supported Platforms


